TMCnet News
SpyCloud 2018 Credential Exposure Report Uncovers Rampant Password ReuseAUSTIN, Texas, Feb. 12, 2019 /PRNewswire/ -- SpyCloud, the leader in account takeover (ATO) prevention, today released its 2018 Credential Exposure Report, which tallies the compromised credentials and personally identifiable information (PII) recovered by the company over the last year and identifies trends in online security habits and the data criminals tend to steal and use.
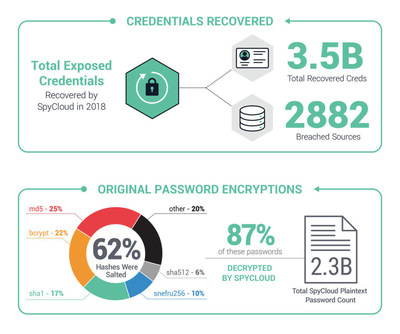
SpyCloud's research team recovered 3,457,017,136 exposed sets of online account credentials and PII from 2,882 different sources, many of which were high-profile data breaches that led to credentials going up for sale on dark web forums and marketplaces. Over 2.6 billion of those credential sets included a password. Based on SpyCloud's analysis of the leaked data, at least 24 percent of users recycled a password, with an overwhelming 90 percent of that segment reusing an exact match as far as spelling, capitalization, special symbols and arrangement. Another 7 percent of those usrs just added one or two numbers onto the end of their preferred, recycled password. Inadequate password hygiene makes it significantly easier for criminals to engage in credential stuffing and resulting ATO. "Account takeover facilitated by weak or stolen passwords is still one of the leading causes of fraud today," said Eric Murphy, vice president of security research at SpyCloud. "Criminals understand how incredibly easy and effective it is to compromise online accounts at scale using software tools freely available for download." SpyCloud was able to use its industry-leading proprietary password cracking technology to decrypt 87 percent of recovered encrypted password hashes. Of those passwords not already visible in plain text, 25 percent used md5, 22 percent used bcrypt, 17 percent used sha1, 10 percent used snefru-256 and 6 percent used sha512. Among plaintext passwords, the most popular was "123456" (favored by more than 39 million users), while "password" appeared as the ill-advised passcode of choice more than 7 million times. Popular sports and teams, country names and large cities commonly made the list of most used passwords on a geographic basis. Interestingly, "anhyeuem" -- Vietnamese for "I love you" -- cracked the top 15 most common plaintext passwords. "One of the easiest ways to mitigate account takeovers is to curtail password reuse across multiple accounts and make passwords difficult to steal or bypass," said Ted Ross, CEO and co-founder of SpyCloud. "Until we instill security-aware culture within organizations and ensure that individuals are consistently practicing good password hygiene spanning both work and personal accounts, ATO and its harsh consequences will persist." To read the full report, interact with a map of the most popular passwords by country or check your company's ATO exposure, visit https://spycloud.com/2018-annual-credential-exposure-report/. About SpyCloud
SOURCE SpyCloud 
|